-
Apple Starts Showing Ads in App Store & Apple Pay Expansion

Apple will start showing ads in the App Store, allowing you to discover more apps for your iPhone. Besides, Apple might also expand its Apple Pay support for more browsers. Let’s discuss the complete details below. On Saturday, Apple announced that ads would be displayed in App Store for the apps, which will also help developers […]
-
GTA 6: New Leaks About Characters & Expected Release Date
GTA 6’s latest leaks and rumors are breaking the internet, and these leaks are significant & detailed. Besides, these leaks are tipped by some well-known tipsters, so it is worth discussing. We all are waiting for the announcement or the official reveal of the next installment of the Grand Theft Auto game series, which admirable RockStar […]
-
WhatsApp Plans New Ability To Notify New Features Directly In App

WhatsApp is reportedly working on an exciting ability to announce new features directly in the app and advise other things, such as privacy and safety. Meta-owned WhatsApp is already working on many features, and now in the latest beta update, this new feature has shown up, so let’s discuss all the details. WhatsApp Would Soon […]
-
How to Use UUP Dump to Download Windows 11 ISO File

Well, you have multiple ways to download Windows 11 ISO files. You can grab the ISO file directly from Microsoft’s official website, which requires a Microsoft account. Or else, you can use the media creation tool to download an ISO file on your device. However, the problem is that the Media Creation tool and Microsoft’s […]
-
Google Play Store Now Shows More Precise Data Collection Detail

Google has removed its recently released App Permissions overview from the Play Store and introduced a new section named Data Safety. This new section accurately details what data the app collects and why. Google Play Store’s new detailed section is available for many users, and this section will make them confident about downloading apps from […]
-
WhatsApp Releases New MacOS App Built With Catalyst
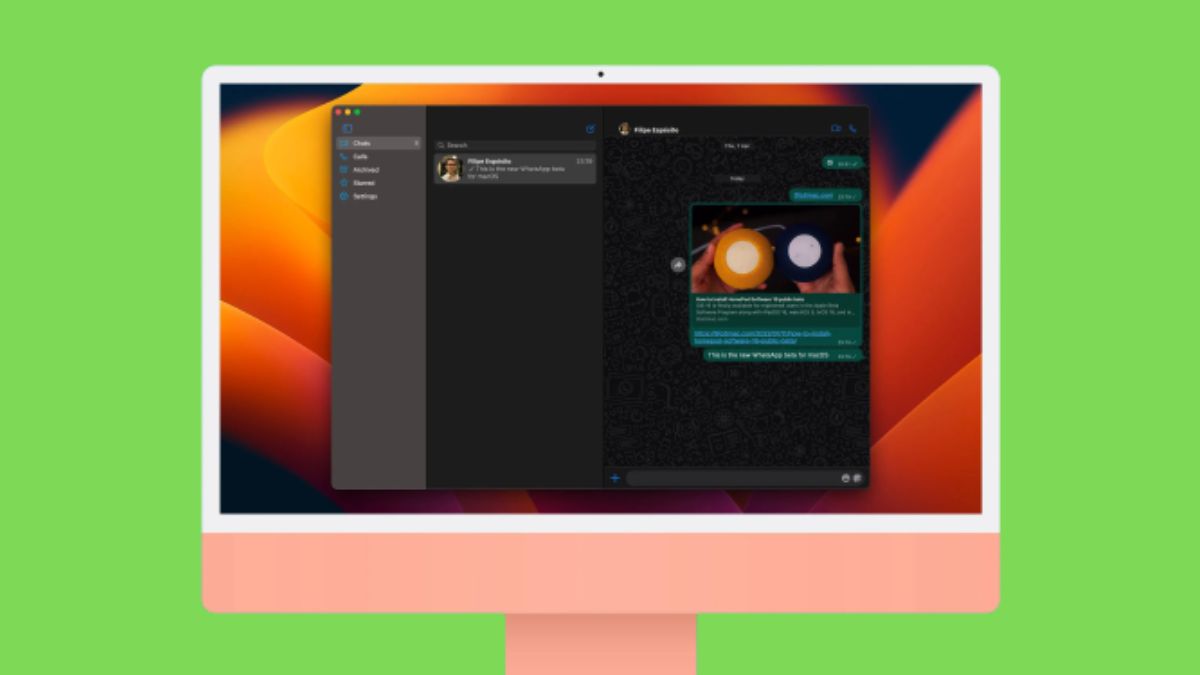
Last year, Whatsapp released a native Universal Windows Platform beta app for Windows. Now, the company is releasing a beta version for macOS and iPadOS. Currently, it is available for a small number of people to test the feature. It is a new macOS app that is built on Catalyst technology. This app is based on Whatsapp […]
-
iPhone 14 Leaked Third-Party Cases Shows Larger Camera Bump

iPhone 14’s leaked third-party cases images show some design changes and camera lens size enlargement in the upcoming models. Let’s discuss every noted from these cases image. iPhone 14 story has already described its struggle and how the company is facing challenges in its production in China. But, this iPhone is also getting this many […]
-
Elon Musk Wants To Back Off From $44 Billion Twitter Deal

According to Reuters, Elon Musk now wants back off from the Twitter buying deal for some reasons, and as said, the social media giant will take legal action to enforce the merger agreement. On Friday afternoon, Musk’s team informed the Securities and Exchange Commission that Twitter had done a “material breach” in the agreement and also, in negotiations, […]
-
Asus Launched Gaming Beast: ROG Phone 6 & 6 Pro With Back Display

Asus has launched its ‘ROG Phone 6’ with two new models like last year and its most powerful gaming smartphone. Let’s discuss every possible detail, including its pricing and availability. As we all know, every year, Asus only launch one flagship with different models, and gamers highly prefer their smartphones because the Asus ROG series […]
-
Apple Watch Series 8 Might Detect Your Fever & Tell You

Apple Watch Series 8 leaked features have already indicated that the Watch stands out from the competition and now reliable Mark Gurman reported that it can also detect your fever. Recently, Mark also suggested another feature regarding the Watch Series 8 which is the “low battery mode” with more enhancement, and you can take it as iPhone’s low battery mode. Apple […]